Further in this series after Azure & OKTA SAML integration, I will be discussing about SAML integration of UAG with Ping IdP. This can be achieved by following the below three steps which are explained in detail below:
- Ping IdP configuration UAG details as per your organization
- Upload SAML Metadata from IDP to UAG
- Configure Horizon Settings on UAG for SAML Integration
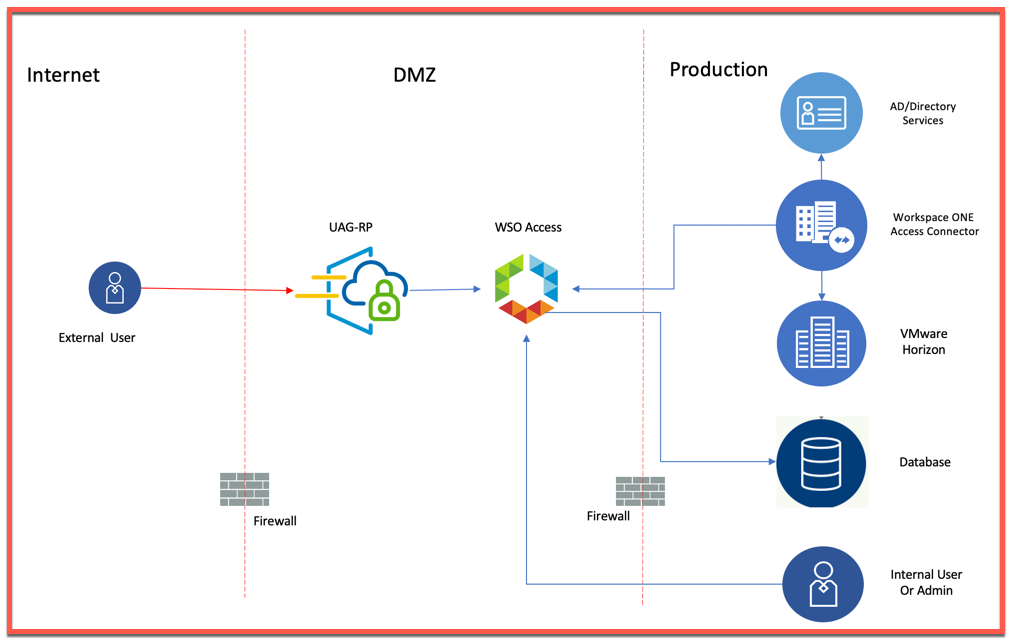
Setup Details:
Horizon 7.11 or higher configured with UAG 3.8 or higher.
Portal ID: https://<PublicIP/DomainName>/portal
Portal SSO URL: https://<PublicIP/DomainName>/portal/samlsso
Ping integrated with with same Ad as does Horizon.
- Log into PingOne IdP admin console and navigate to APPLICATION > My Applications> Add Application
- Under Add Application, click on New SAML Application
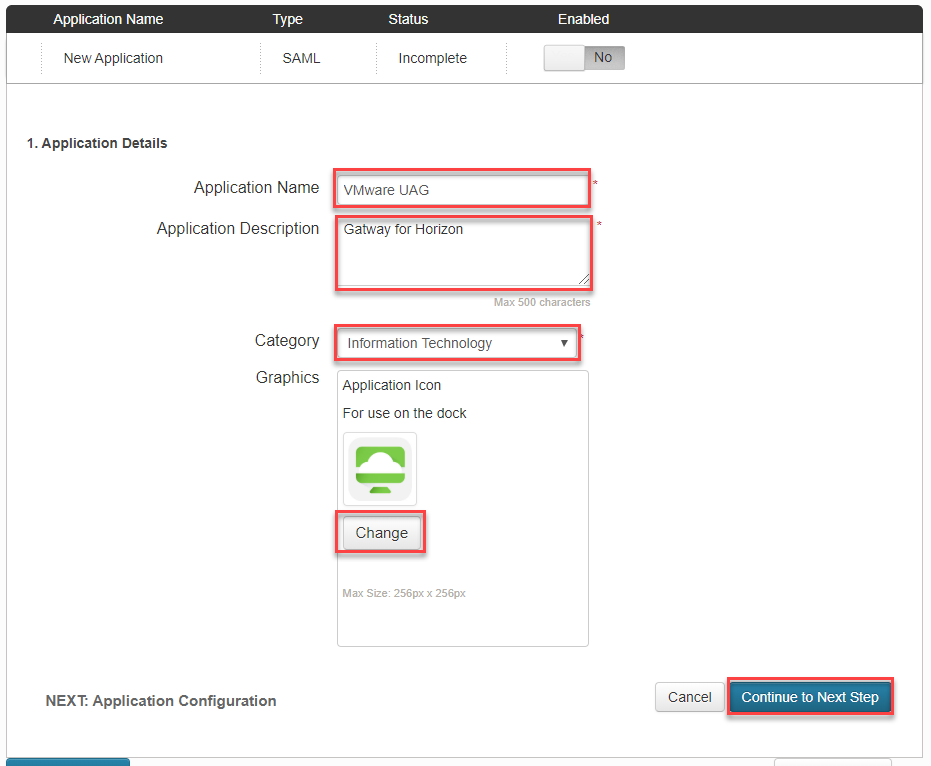
- In Application details, Enter following parameter and click Continue to Next Step.
- Application Name: <Name for your application>
- Application Description: <Description for your application>
- Category: <choose a category from drop down list>
- Graphics: <optional: add an icon file here>
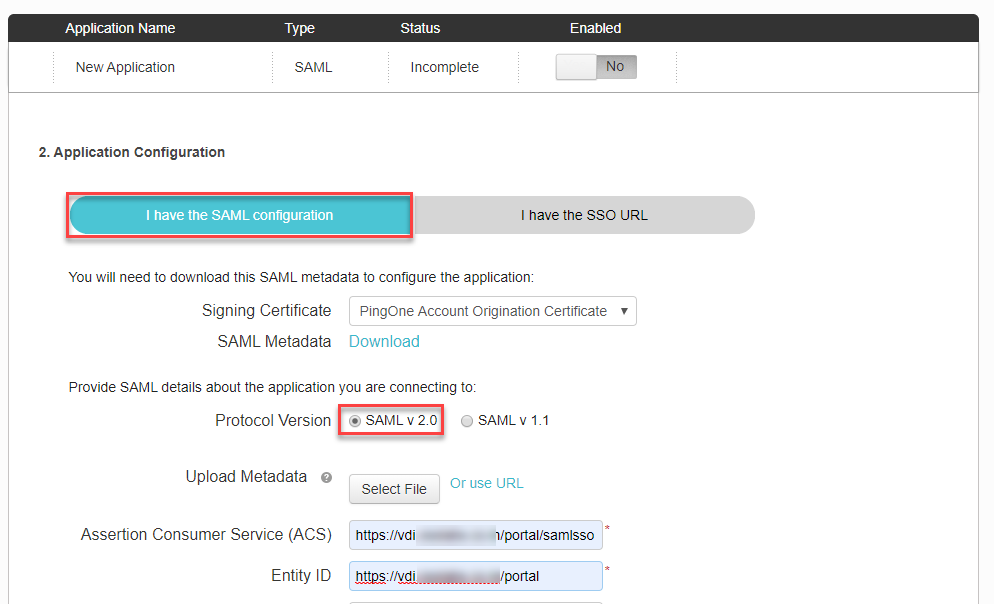
- In Application Configuration, enter below details and click Continue to Next Step.
- Select I have the SAML configuration
- Protocol version: SAML v 2.0
- Assertion Consumer Service: https://<PublicIP/DomainName>/portal/samlsso
- Entity ID: https://<PublicIP/DomainName>/portal
- Leave everything else default.
- In SSO attribute Mapping, click on Add new attribute
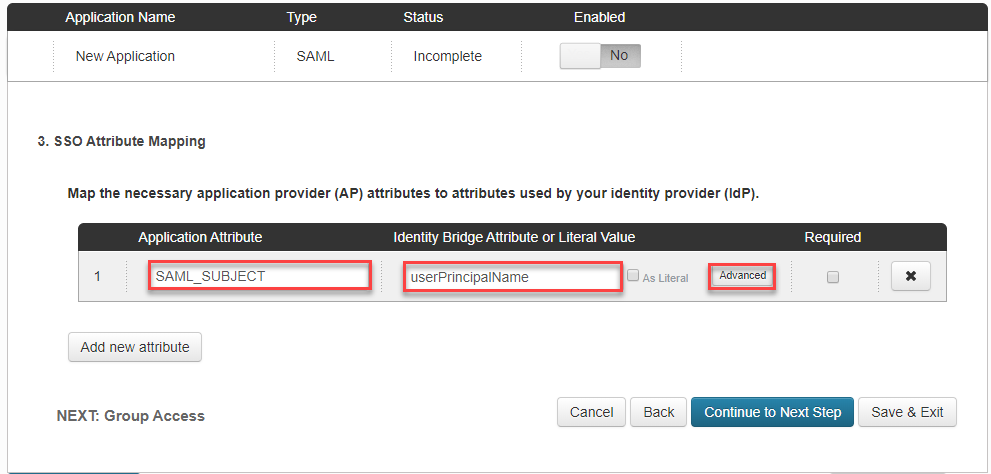
- Enter below data and click on Advanced
- Application Attribute: SAML_SUBJECT
- Identity Bridge Attribute or Literal Value: userPrincipalName
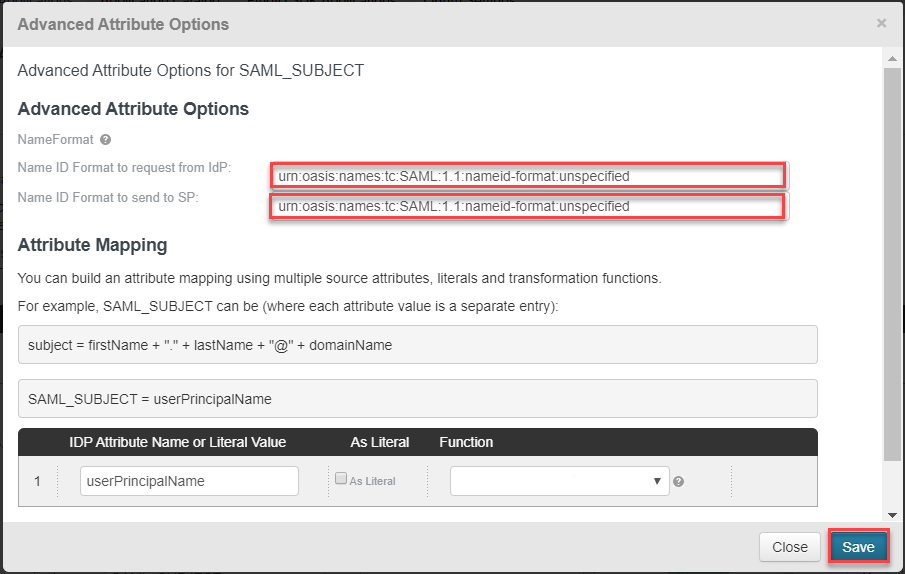
- In Advanced Attribute Options, select the value as shown in snapshot. this will automatically come up as drop down list, no need to type and click on Save
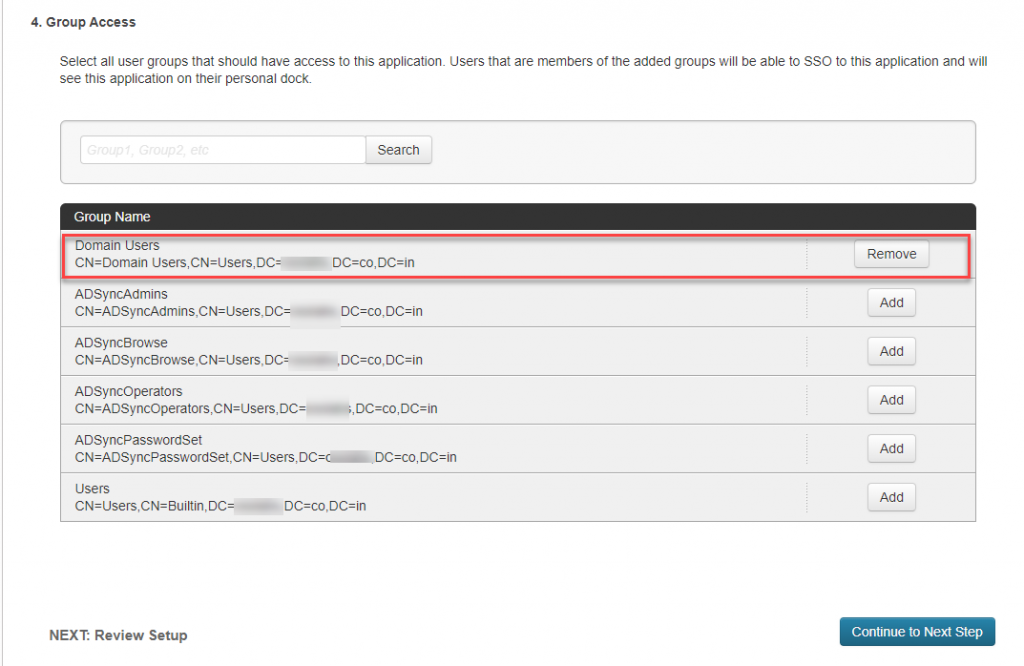
- In Group Access, select the user DN who need to have access to this particular application and click Continue to Next Step.
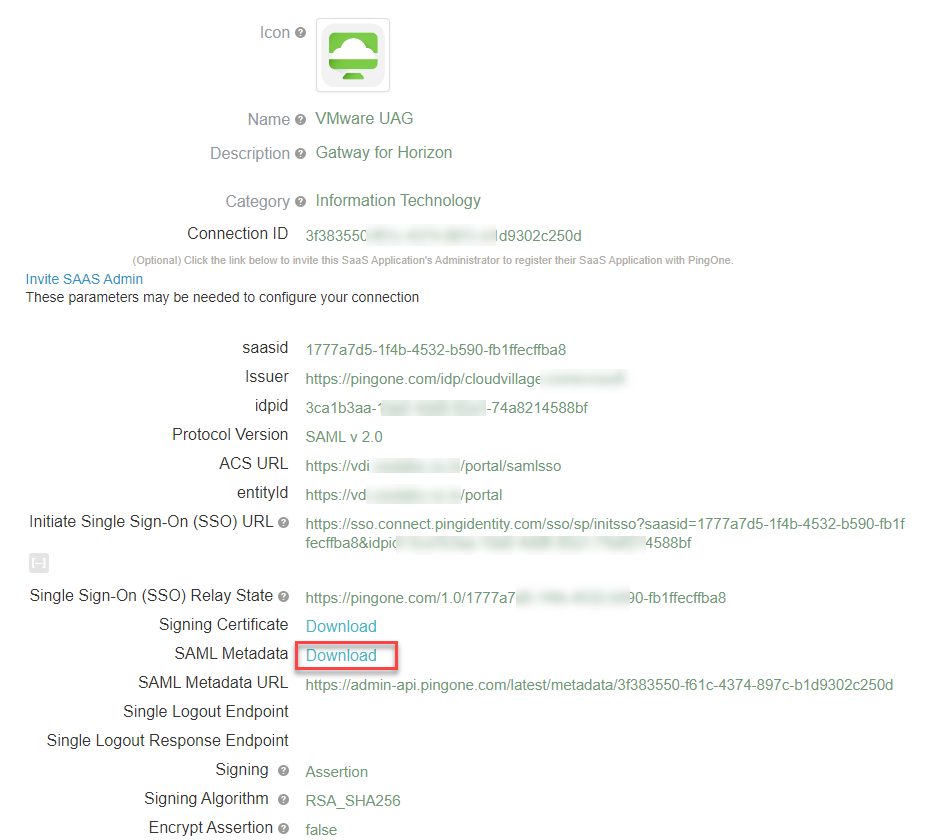
- Verify all the data and Download SAML Metadata from this page. Save the file to be imported in UAG. Click on Finish
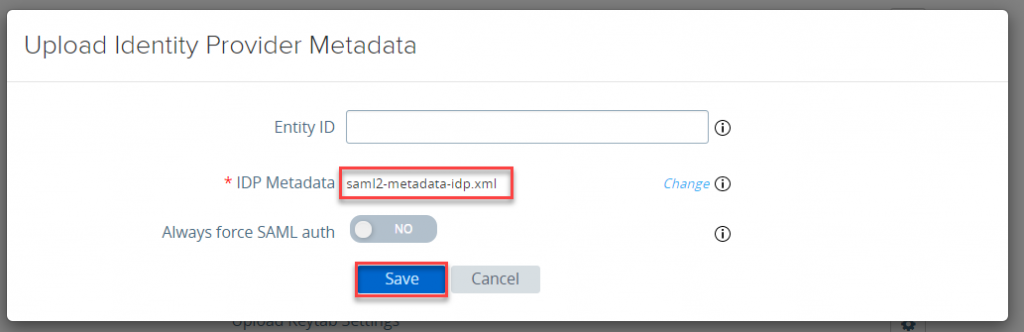
- Login into UAG and click on gear icon for Upload Identity Provider Metadata under Identity Bridging Settings
- Click on Select
- Select the metadata file and click on Save
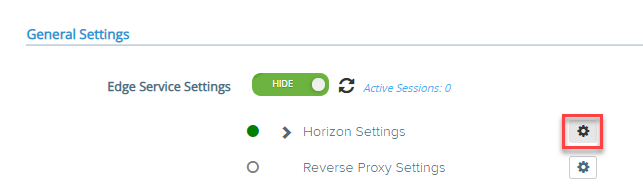
- Navigate the Edge Service Settings and click on gear icon for Horizon Settings
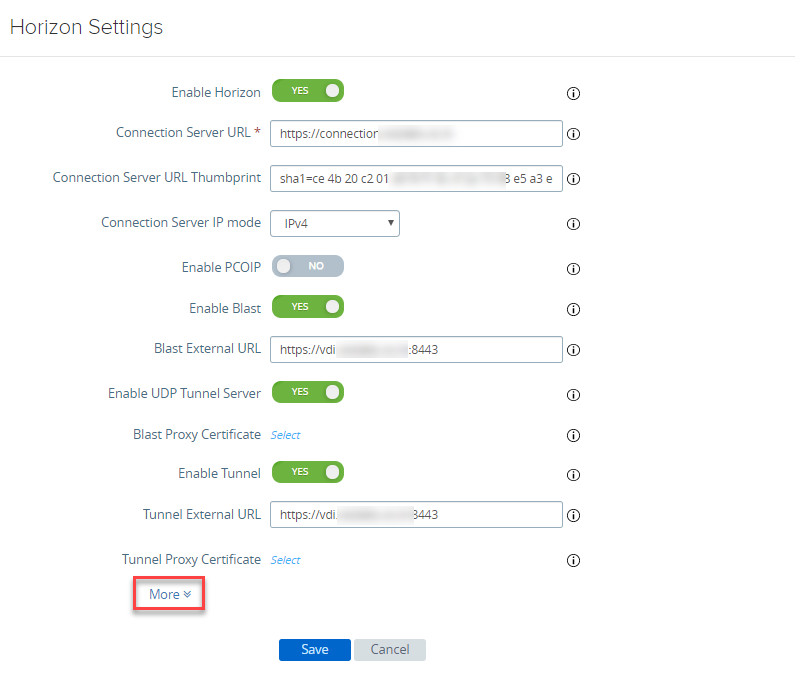
- Scroll down and click on More in Horizon Settings
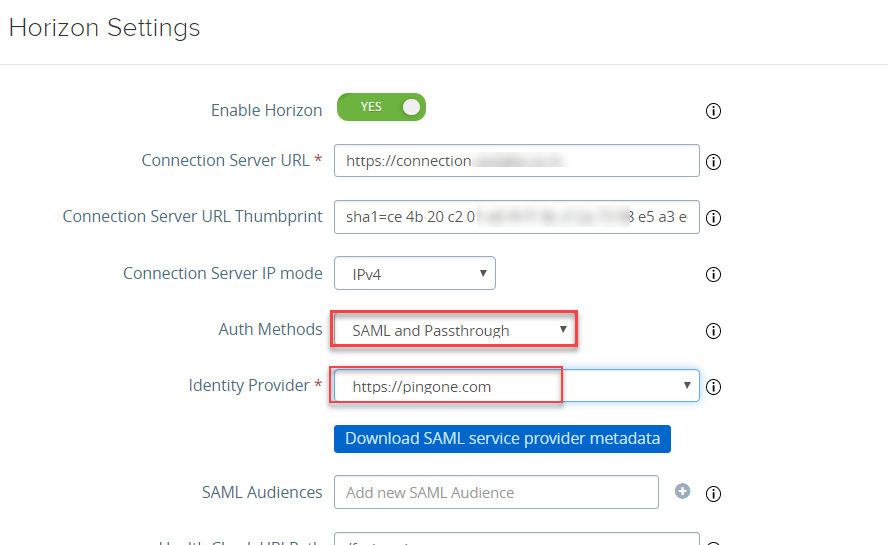
- You will see new parameters, select the below mentioned value and Click on Finish.
- Auth Methods: SAML or SAML and Passthrough (Depeding on usecase)
- Identity Provider: https://pingone.com
- With this we are done with SAML Integration of UAG with PingOne identity provider. You can now test your application. in case you want to leverage on MFA, same need to be enabled on PingOne for desired users and policy need to be created for the same.