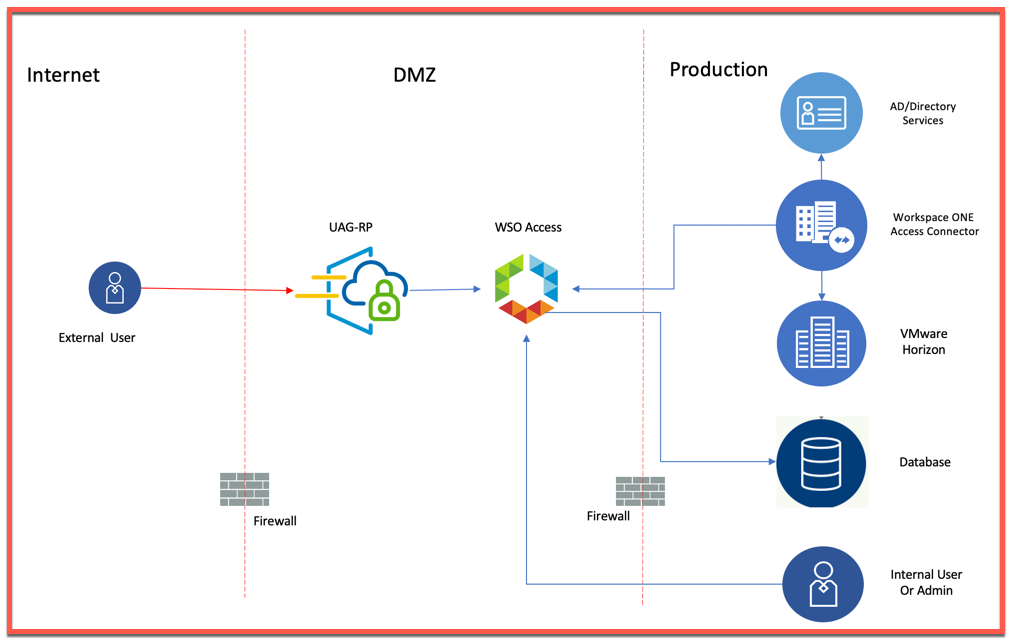
With the surge in work from home requirements due to recent Covid-19 situation, Customers are looking for methods to secure their environment access from Internet. One of the solution from VMware EUC portfolio is VMware Horizon VDI which is being widely leveraged for secure work from home environment and to provide secure access to this solution there are multiple ways:
- SAML integration with Third-Party IdP Azure, OKTA, Ping etc.
- 2FA with RADIUS/RSA
If you are using any of the SAML 2.0 identity provider, you can integrate that to UAG which is a gateway component for Horizon Solution. In this blog, I will be discussing about SAML integration of UAG with Azure IdP. This can be achieved by following the below three steps which are explained in detail below:
- Azure AD IdP configuration UAG details as per your organization
- Upload SAML Metadata from IDP to UAG
- Configure Horizon Settings on UAG for SAML Integration
Setup Details:
Horizon 7.11 or higher configured with UAG 3.8 or higher.
Portal ID: https://<PublicIP/DomainName>/portal
Portal SSO URL: https://<PublicIP/DomainName>/portal/samlsso
Azure AD integrated with with same Ad as does Horizon.
- Login to Azure account and navigate to Azure Active Directory, in Overview, click on Enterprise applications
- Click on New application
- Click on Non-gallery application
- Type desired name for the application and click Add
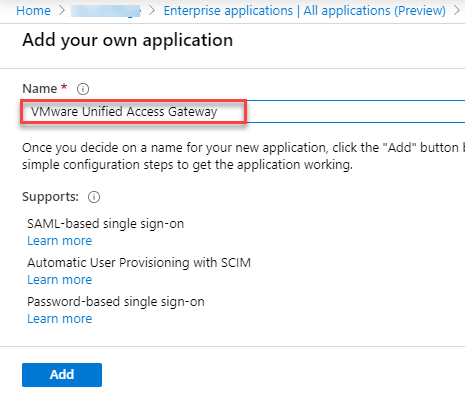
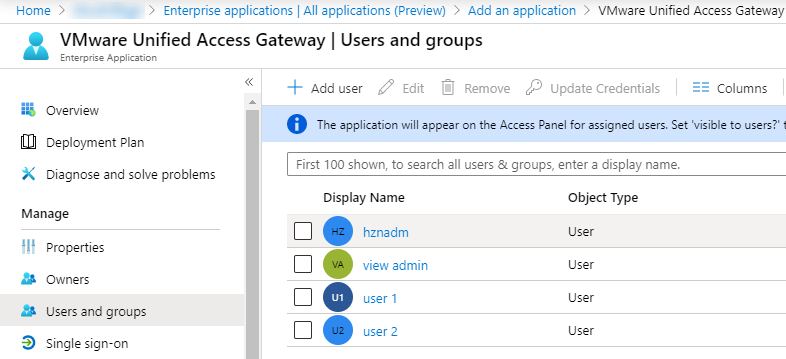
- Once application is created, select on Properties under Manage and click on 1. Assign users and groups
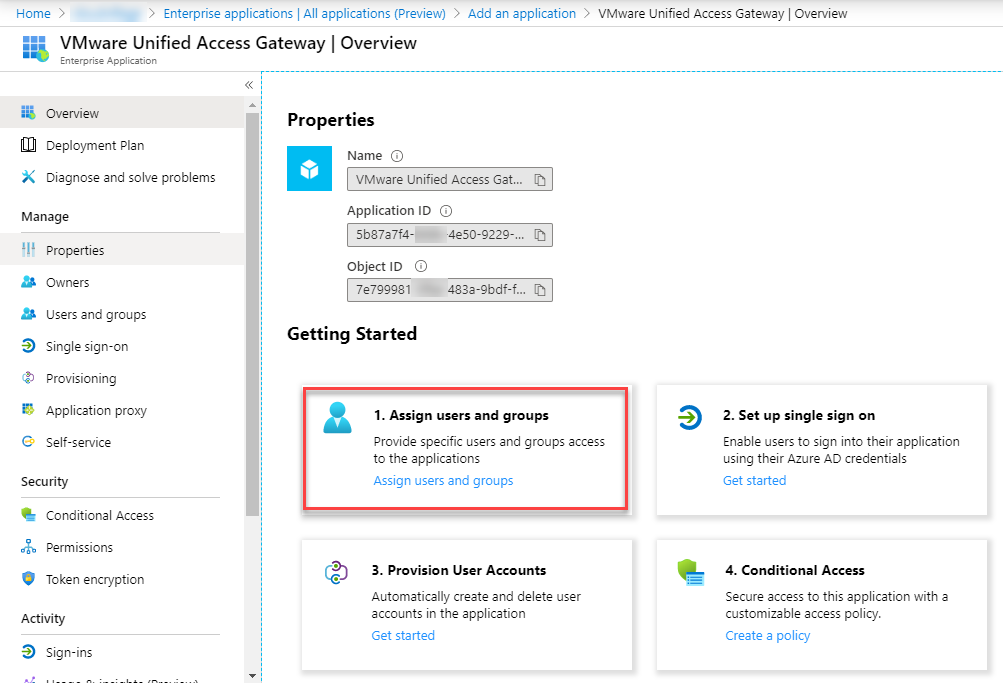
- click on Add user
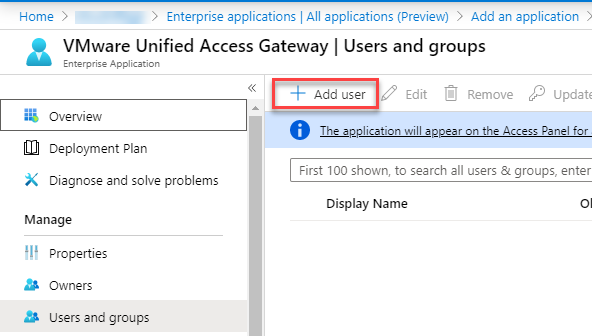
- Click on user and groups and add required users for the application and click on Select
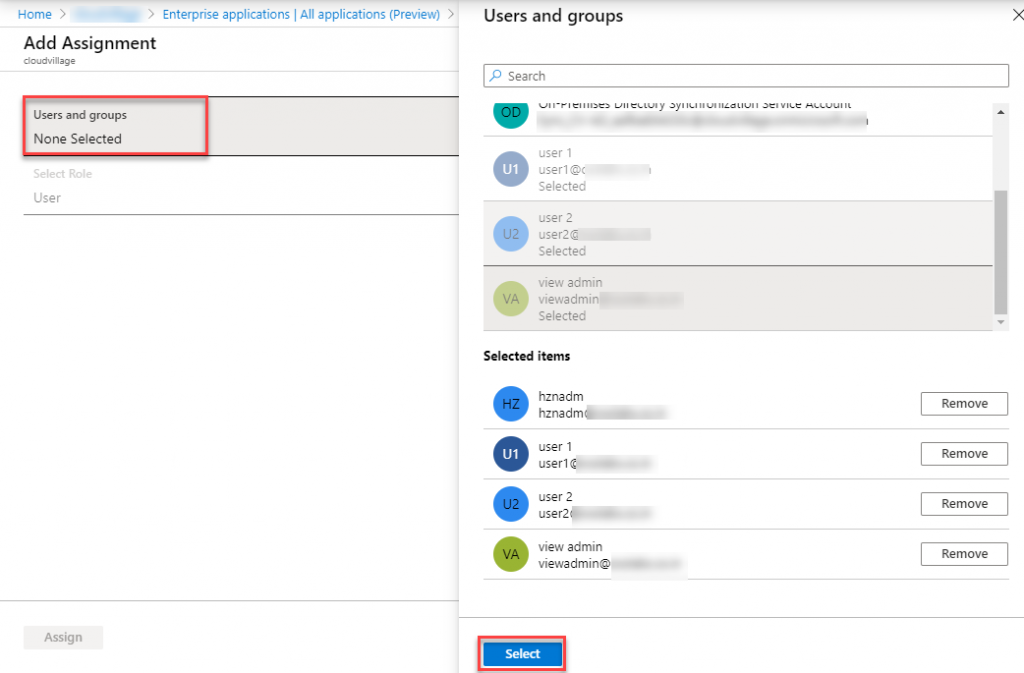
- Click on Assign and verify all the users are added to application.
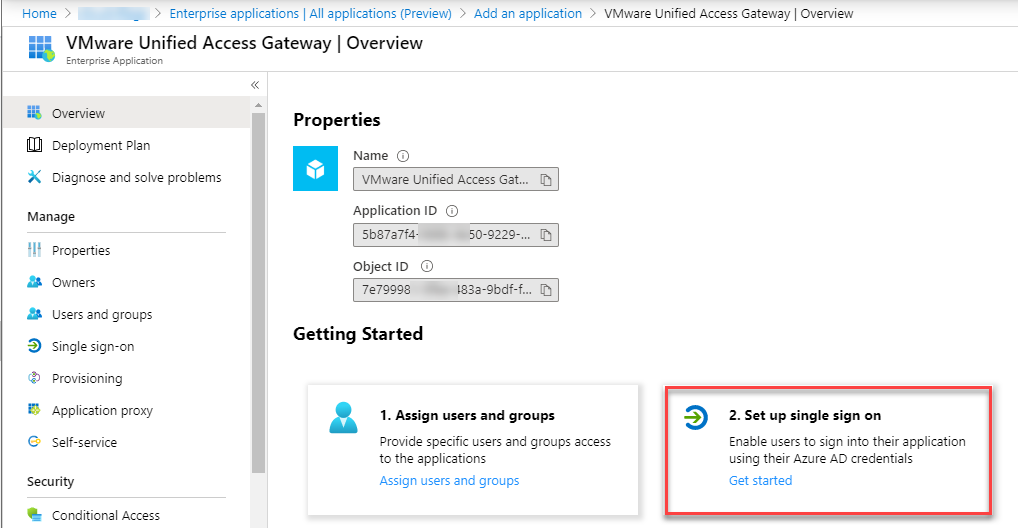
- In Overview, click on 2. Set up single sign on
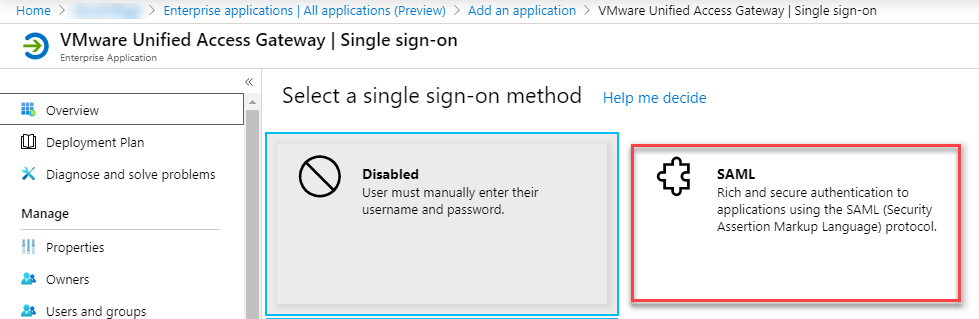
- Click on SAML
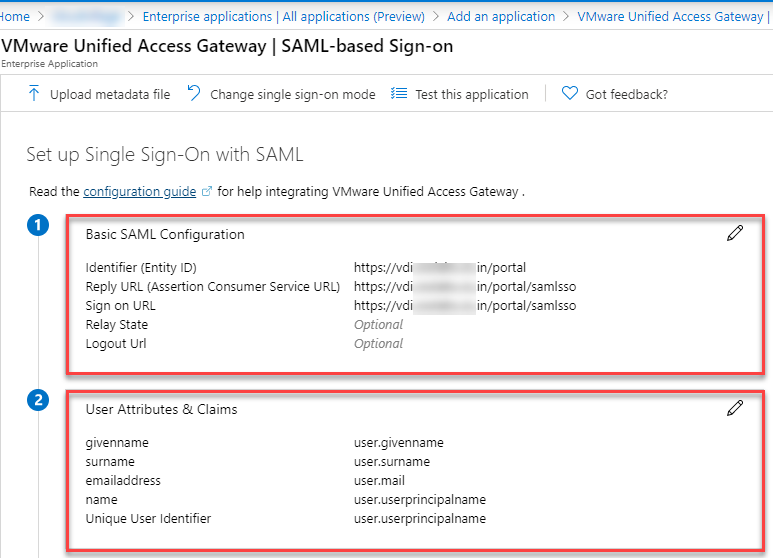
- Enter the value for below parameters and click Save
- Identifier (Entity ID): https://<PublicIP/DomainName>/portal
- Sign on URL: https://<PublicIP/DomainName>/portal/samlsso
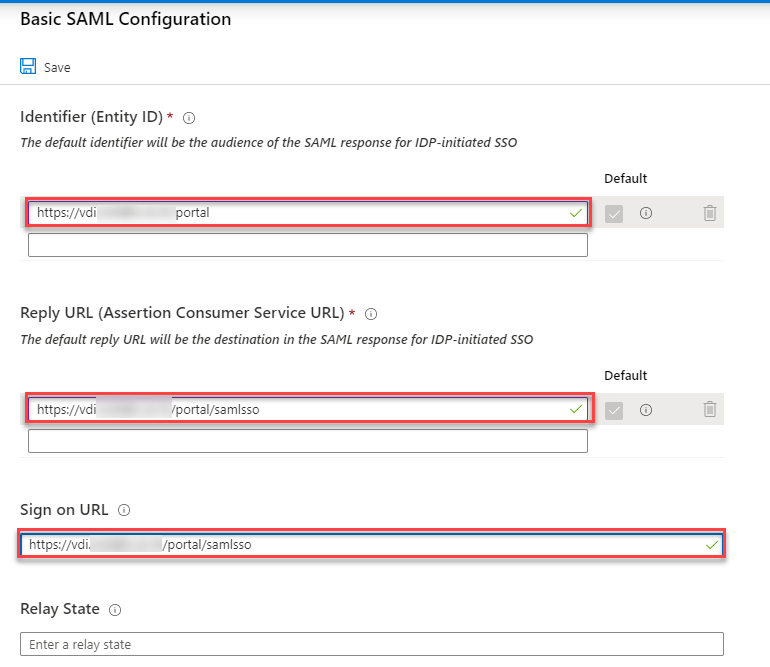
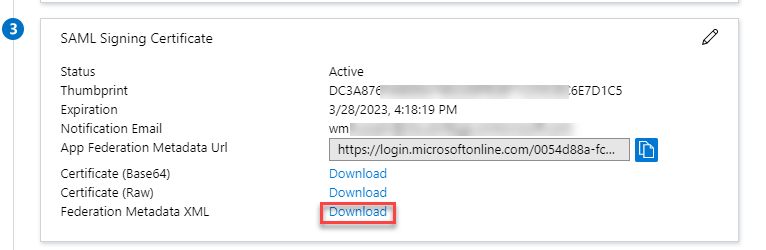
- Verify the details and download the Federation Metadata XML. Save this file as it will be used in UAG configuration.
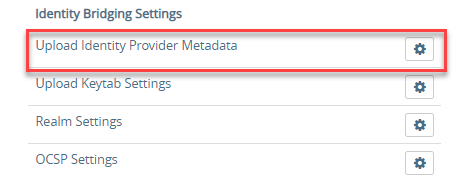
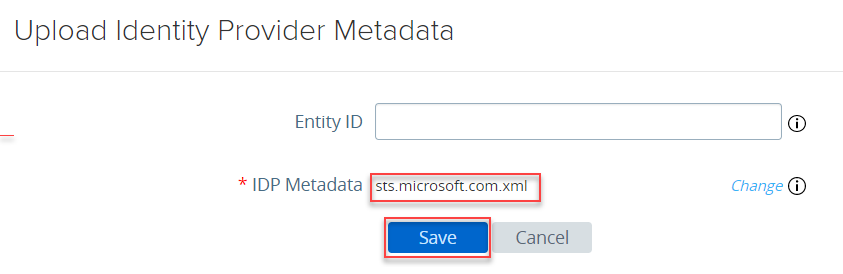
- Login into UAG and click on gear icon for Upload Identity Provider Metadata under Identity Bridging Settings
- Click on Select
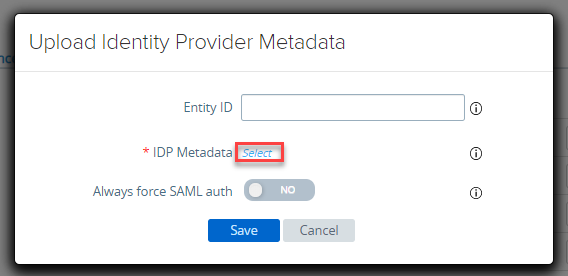
- Select the metadata file and click on Save
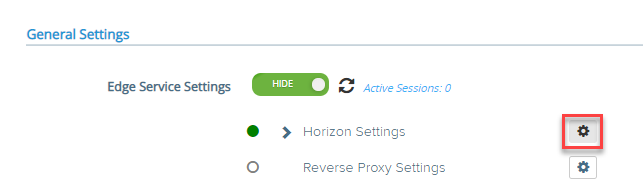
- Navigate the Edge Service Settings and click on gear icon for Horizon Settings
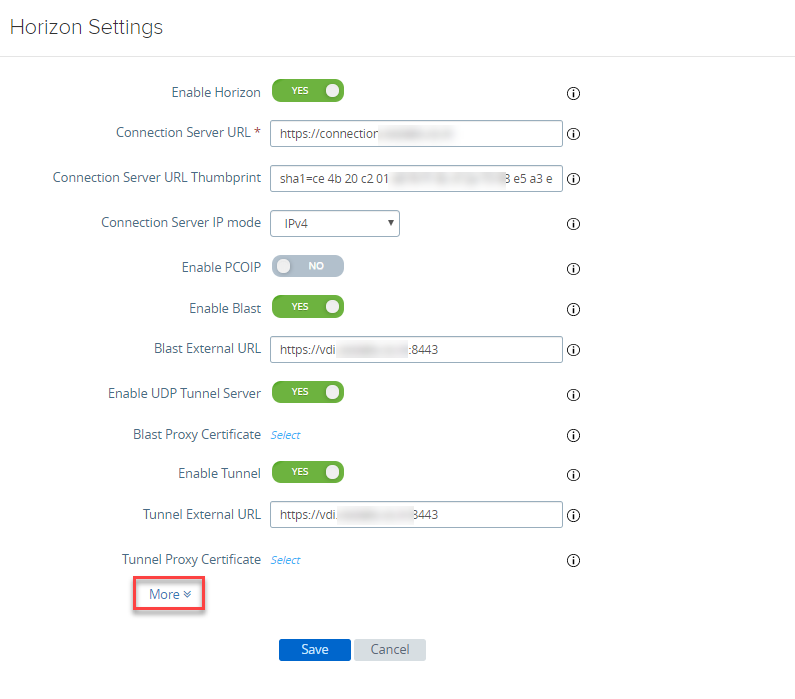
- Scroll down and click on More in Horizon Settings
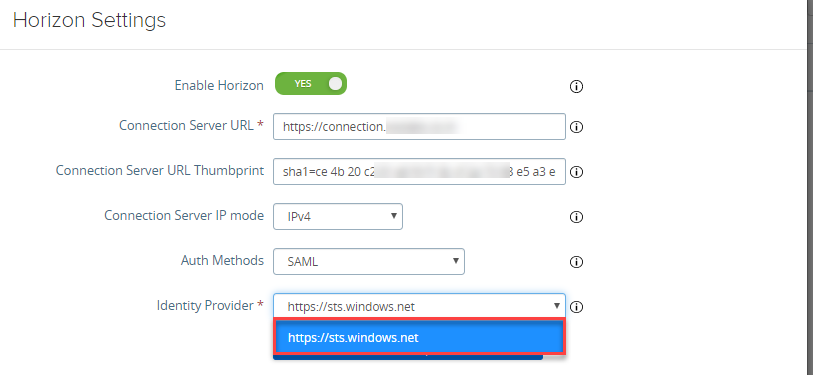
- You will see new parameters, select the below mentioned value and Click on Finish.
- Auth Methods: SAML or SAML and Passthrough (Depeding on usecase)
- Identity Provider: https://sts.windows.net
With this we are done with SAML Integration of UAG with Azure identity provider. You can now test your application. in case you want to leverage on MFA, same need to be enabled on Azure for desired users and policy need to be created for the same.