Hi Everyone, in this forth part of VIDM series, I am going to explain how you are going to authenticate users who are coming from Internet.
Kerberos & Password methods uses connector which is deployed in local LAN and wont be available over Internet. For users who don’t have direct access to connector have to use some other means of authentication. VMware Identity Manager performs the authentication on behalf of user over outbound connection created between connector and VMware Identity Manager.
We are going to discuss below two authentication methods
- Password (Cloud deployment)
- Certificate (Cloud Deployment)
Lets configure, Password (Cloud deployment).
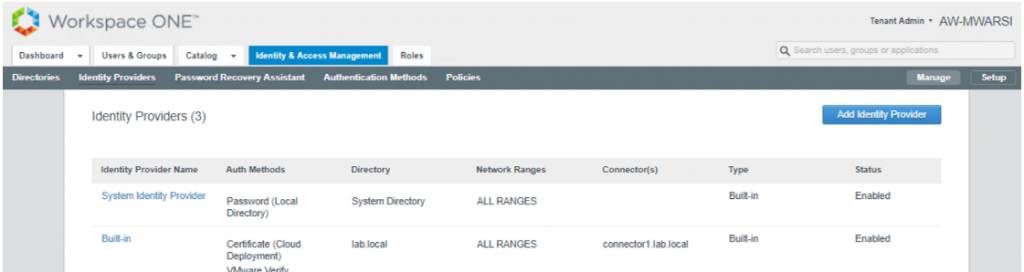
- Login to VMware Identity Manager admin console and navigate to Identity & Access Management > Manage > Identity Providers.
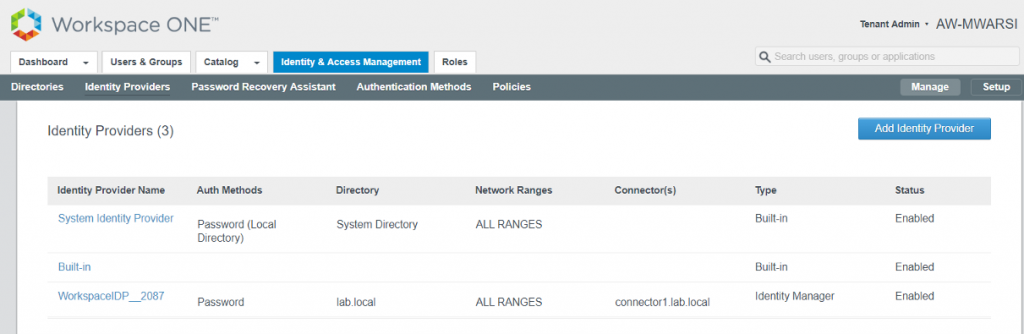
- Notice that there are no Auth Methods, Directory or Connector is associated with Built-in IDP.
- Click on Built-In IDP. Select the directory (lab.local) & select Connector from Add a Connector drop down list. Click Add Connector.
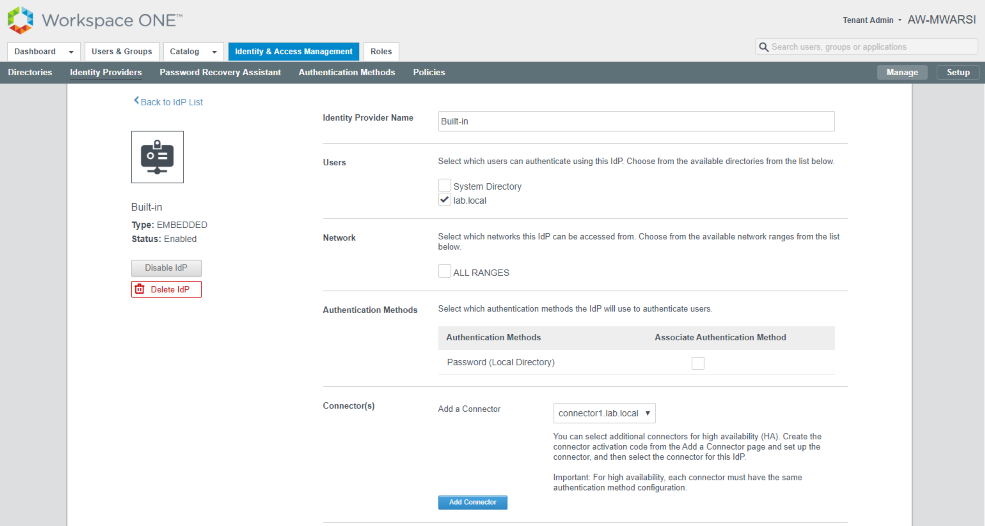
- Once, Connector is successfully added, you will see a new option Connector Authentication Methods available which shows Password (Cloud deployment) authentication option. Select that option and click Save
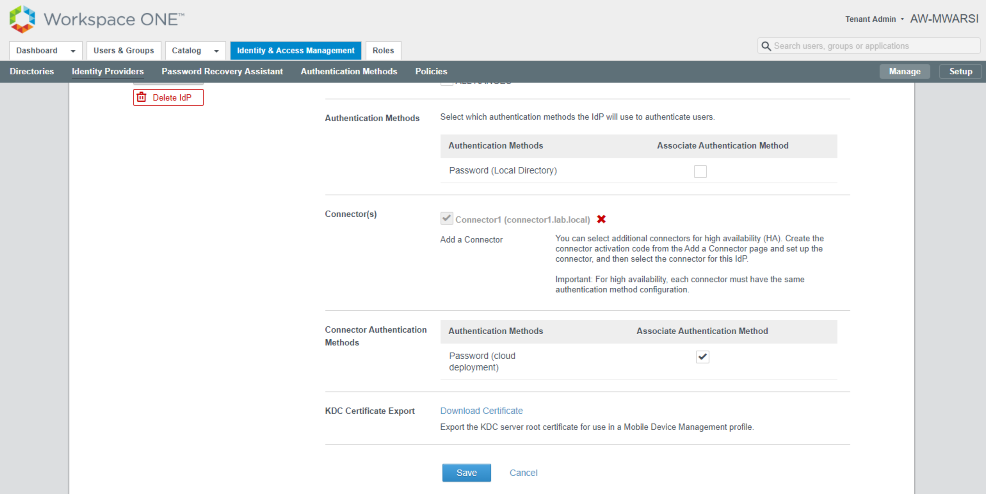
- Verify that Built-In IDP now have directory, Connector and auth method.
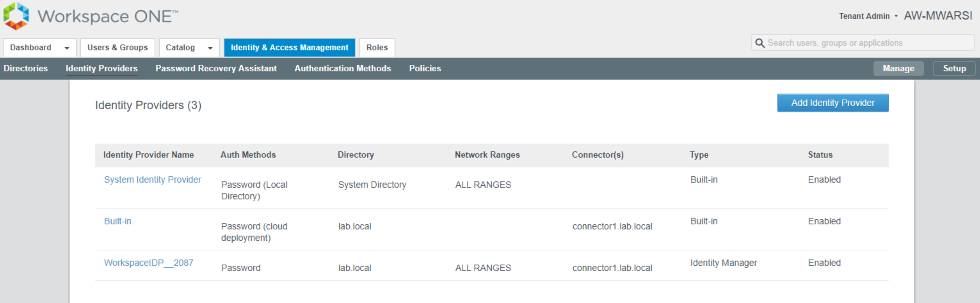
- Next, we have to update the default policy to use Password (Cloud deployment). Navigate to Identity & Access Management> Manage> Polices. Click on Edit Default Policy> Configuration > Edit Policy Rule and select Password (Cloud deployment) from drop-down list for authenticate using.
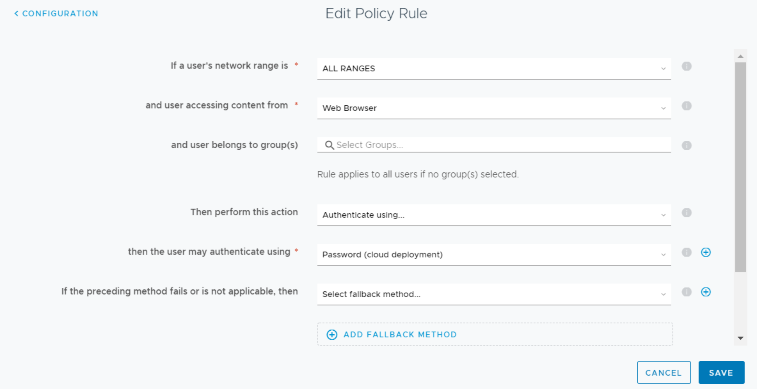
- Click on Save & Finish Edit Policy Wizard and test the auth method.
- Login to any windows machine joined to domain with test user. Launch IE/Chrome and access the VMware Identity Manager portal it will prompt for credentials but you will notice on URL field, it won’t get redirected to Connector URL for authentication as happened for Kerberos and Password based authentication.
- Login to VMware Identity Manager admin console and navigate to Dashboard>Reports> Audit Events and filter Type with Login. It shows the method used to login was Password (Cloud deployment)
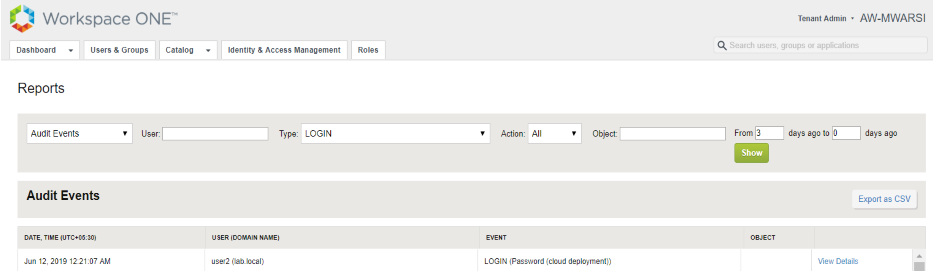
Note: This method will work for any user coming for internet or Intranet. We have not discussed about network range to minimize the complexity and didn’t intend to lose the focus from authentication.
Lets jump on to Certificate (Cloud deployment) authentication method.
In order to do certificate based authentication, we need to provide user with a CA signed user certificate and upload Root & Intermediate Certificate in VMware Identity Manager so it can verify user’s certificate.
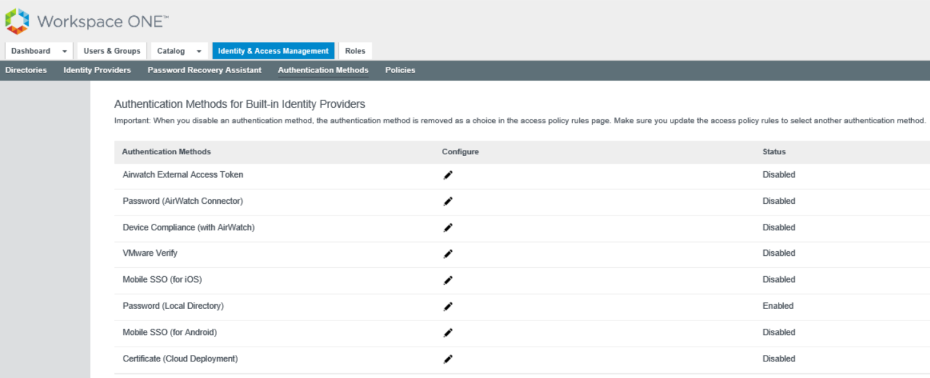
- Login to VMware Identity Manager admin console and navigate to Identity & Access Management > Manage > Authentication Methods and click on Pencil icon to configure Certificate (Cloud deployment).
- Click on Select file to upload Root and intermediate certificate. Locate the CA Root certificate and upload.
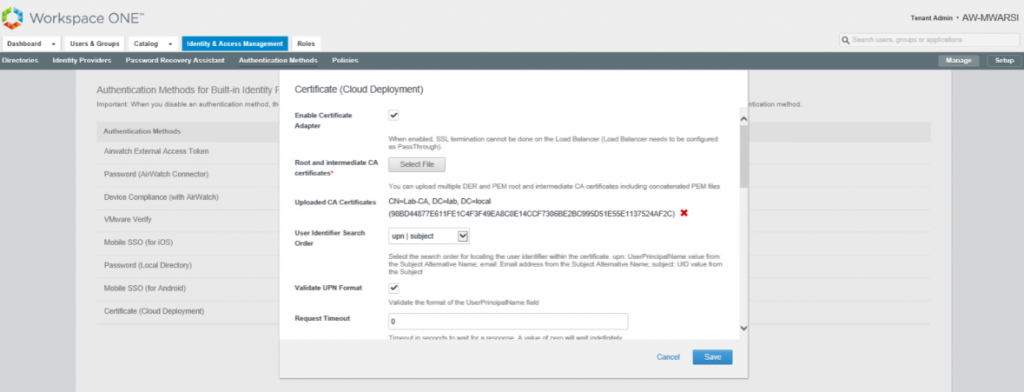
- You can verify certificate under Uploaded CA Certificates. Click on Save.
- Now, we need to configure IDP to use Certificate based authentication. Navigate to Identity & Access Management > Manage > Identity Providers and click on Built-In IDP. You will notice Certificate (Cloud deployment) authentication method is available. Select it and click on Save.
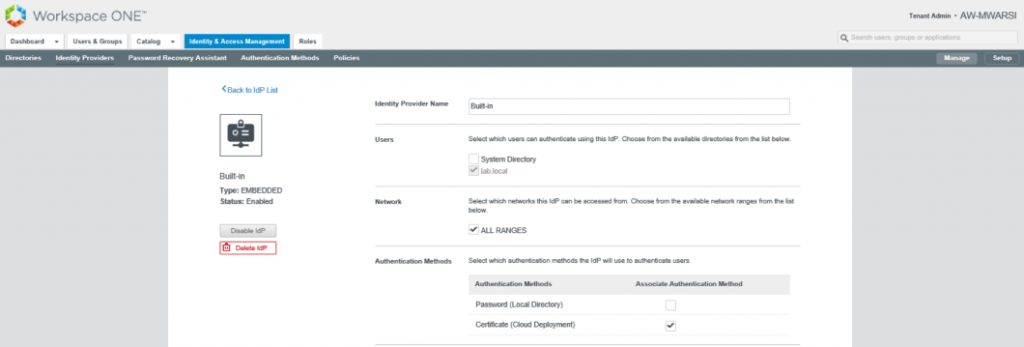
- Verify that Certificate (Cloud deployment) is available under Authentication Methods against Built-In IDP.
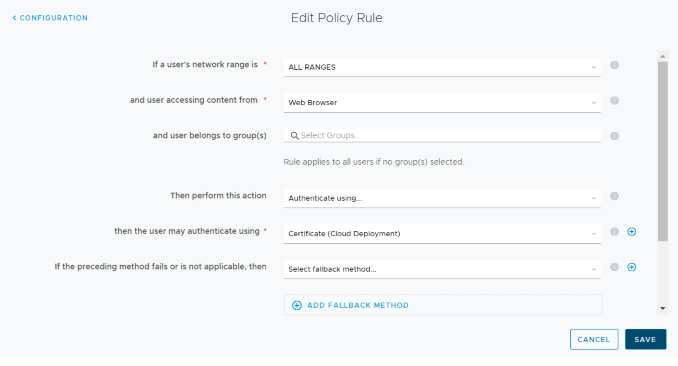
- Next, we have to update the default policy to use Password (Cloud deployment). Navigate to Identity & Access Management> Manage> Polices. Click on Edit Default Policy> Configuration > Edit Policy Rule and select Certificate (Cloud deployment) from drop-down list for authenticate using. Click on Save.
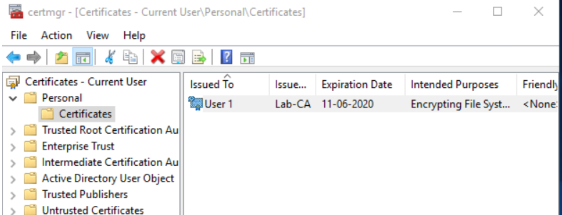
- Login to end user machine and Request/Import a user certificate in certificate store.
- Launch IE/Chrome in your system where you have User certificate imported and access the VMware Identity Manager Portal. You will get a prompt to use certificate to authenticate. Click OK and you will be successfully logged into portal.
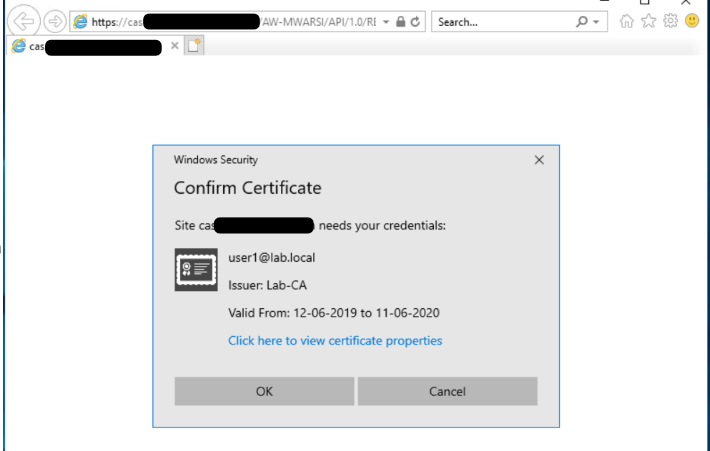
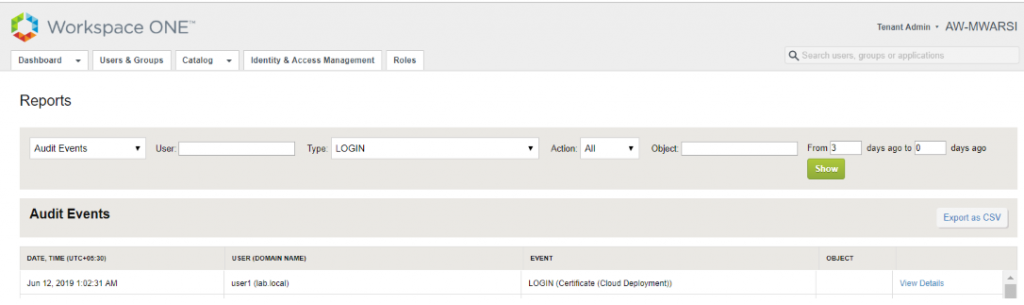
- Login to VMware Identity Manager admin console and navigate to Dashboard>Reports> Audit Events and filter Type with Login. It shows the method used to login was Certificate (Cloud deployment)
Next, we will talk about configuring multi-factor using VMware verify in Part 5 of this series.
Thanks for reading, let me know your feedback.
Is there MTLS here? Can the client verify the server is who it says it is?
What kind of x509 extensions are required?