Hi, In last article I explained how you can integrate Horizon with VMware Identity Manager and within one catalog, users can access their On-premises or SAAS based webapps as well as Horizon based Applications and desktops. Also, we have seen how we can access the desktop resource seamlessly.
Now, there is one more caveat here, if we login to VMware Identity Manager using any other authentication method apart from Username/Password or Smart card login, this seamless login behavior changes which I have explained below. TrueSSO is answer to mitigate that changed behavior and keep the users experience same. TrueSSO concept is very well explained in this article and hence I am not going to explain again.
To carry out this demonstration, I have following implemented and configured:
Microsoft Enterprise CA
VMware Identity Manager with AD & Radius Configured
Horizon 7.x deployment with a RDSH Manual Farm
Horizon Enrollment server
Here, I am going to use Radius for authentication and will see what are impact and how that is to be rectified.
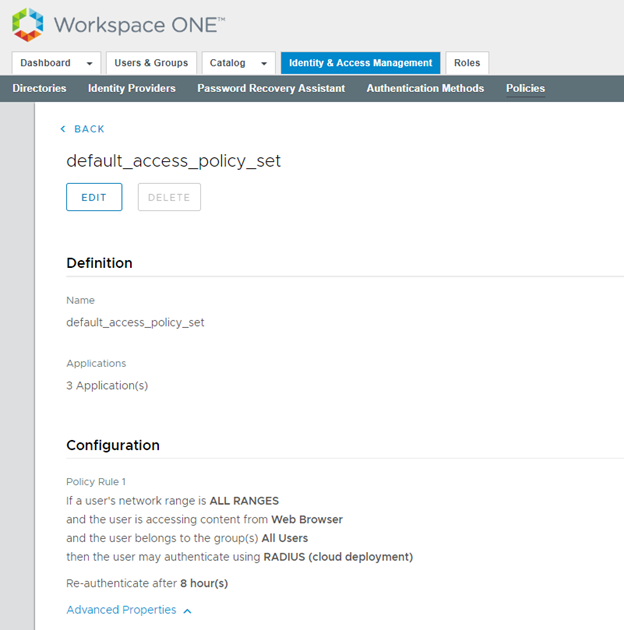
- Login to VMware Identity Manager and navigate to Identity & Access Management>Manage>Policies. Edit default policy to select Radius (Cloud Deployment) as authentication method.
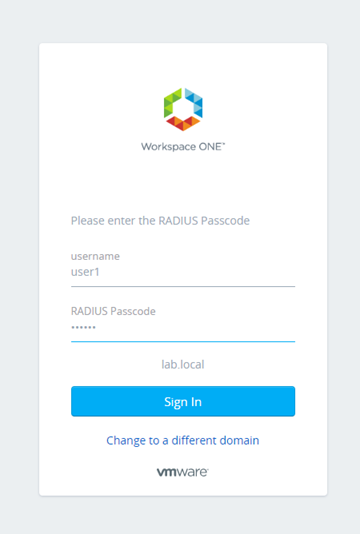
- Launch the browser and login with Username as Radius Passcode.
- Click on Horizon Desktop.
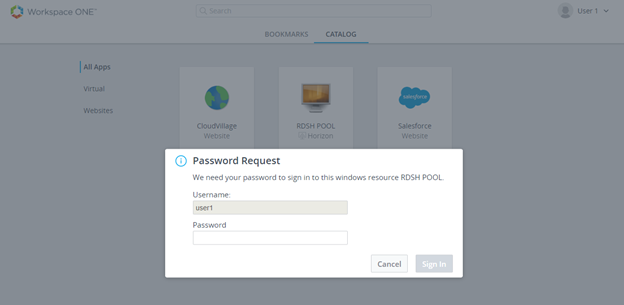
- You will be requested to enter password. Here is difference in user experience.
- Once, you enter the password, you will be presented with desktop.
- To mitigate this extra hop, we need to configure Microsoft CA. If you don’t have Enterprise Certificate authority deployed, you can follow this article where it is clearly explained how to deploy MS CA. Generally it will be taken care by Enterprise AD team at customer sites.
- Next you have to create two template which are to be used for TrueSSO certificates as well as Enrollment server which is again explained in this article. You can share this again with MS CA team to follow
- Login to Enrollment server with admin rights and run certlm.msc in RUN window. It will open Certificate – Local Computer. Right click on Personal folder and Request New Certificate under All Tasks.
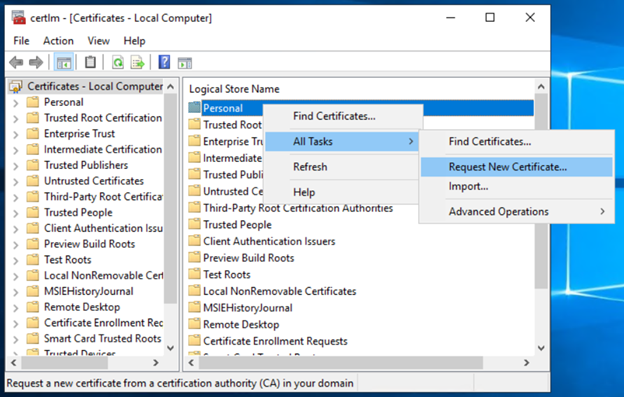
- Click Next on Select Certificate Enrollment Policy
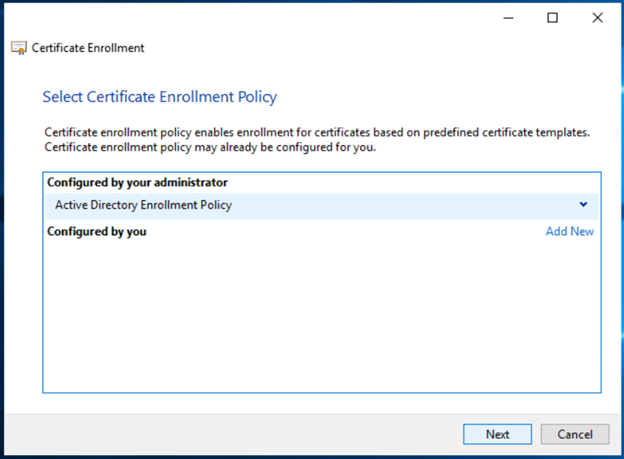
- Select Enrollment Agent (Computer) which is published by your Enterprise CA admin as per the above article shared as prerequisite. Click on Enroll
- Once, Enrollment is successful, click on Finish.
- Now, we need to install the binaries for Enrollment server. This is standard installation and Horizon Connection server binaries are used for this. Only difference is type of Horizon Connection Server instance which you have to select as Horizon 7 Enrollment Server and complete the installation.
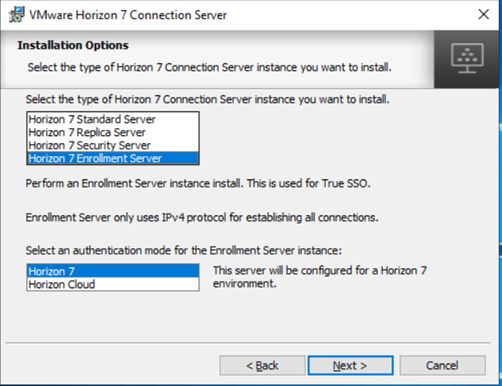
- Next we have to Export the Enrollment Service Client Certificate from the connection server.
- Login to Horizon Connection Server with admin rights and launch certlm.msc in RUN window
- In left pane, expand the VMware Horizon View Certificates folder and select the Certificates folder.
- In the right pane, right-click the certificate file with the friendly name vdm.ec, and select All Tasks > Export
- In the Certificate Export wizard, accept the defaults, including leaving the No, do not export the private key radio button selected
- Save the certificate with some suitable name.

- Now, we need to import the Enrollment Service Client Certificate on the Enrollment Server
- Login to Horizon Enrollment Server with admin rights and launch certlm.msc in RUN window
- In the left pane, right-click the VMware Horizon View Enrollment Server Trusted Roots folder and select All Tasks > Import
- In the Certificate Import wizard, follow the prompts to browse to and open the EnrollClient certificate file
- Follow the prompts and accept the defaults to finish importing the certificate.
- Right-click the imported certificate and add a friendly name such as vdm.ec
- Login back to Horizon Connection Server to configure it for TrueSSO
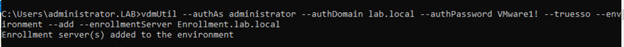
- On a Connection Server in the cluster, open a command prompt and enter the command to add an enrollment server.
vdmUtil –authAs administrator –authDomain lab.local –authPassword VMware1! –truesso –environment –add –enrollmentServer Enrollment.lab.local
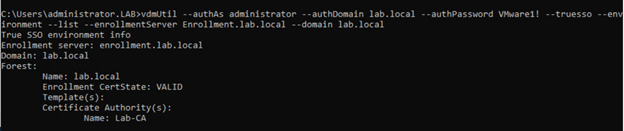
- Enter the command to list the information for that enrollment server.
vdmUtil --authAs administrator --authDomain lab.local --authPassword VMware1! --truesso --environment --list --enrollmentServer Enrollment.lab.local --domain lab.local
- Enter the command to create a True SSO connector, which will hold the configuration information, and enable the connector
vdmUtil --authAs administrator --authDomain lab.local --authPassword VMware1! --truesso --create --connector --domain lab.local --template TrueSSO --primaryEnrollmentServer Enrollment.lab.local --certificateServer Lab-CA --mode enabled
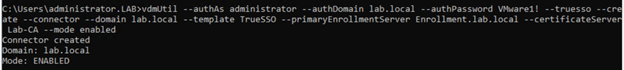
The True SSO connector is enabled on a pool or cluster for the domain specified. To disable True SSO at the pool level, run vdmUtil –certsso –edit –connector <domain> –mode disabled. To disable true SSO for an individual virtual machine, you can use GPO (vdm_agent.adm).
- Enter the command to discover which SAML authenticators are available.
vdmUtil --authAs administrator --authDomain lab.local --authPassword VMware1! --truesso --list --authenticator
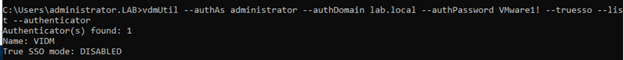
Authenticators are created when you configure SAML authentication between VMware Identity Manager and a connection server, using Horizon Administrator.
The output shows the name of the authenticator and shows whether True SSO is enabled.
- Enter the command to enable the authenticator to use True SSO mode.
vdmUtil --authAs administrator --authDomain lab.local --authPassword VMware1! --truesso --authenticator --edit --name VIDM --truessoMode ENABLED 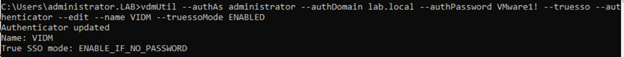
For –truessoMode, use ENABLED if you want True SSO to be used only if no password was supplied when the user logged in to VMware Identity Manager. In this case if a password was used and cached, the system will use the password. Set –truessoMode to ALWAYS if you want True SSO to be used even if a password was supplied when the user logged in to VMware Identity Manager.
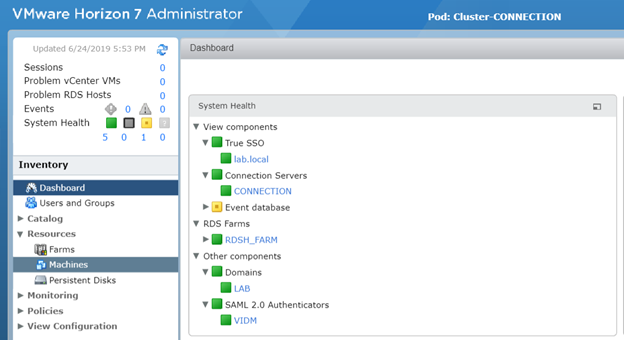
- Login the Horizon Connection server and validate that TrueSSO is not enabled and you can see it under System Health in Dashboard
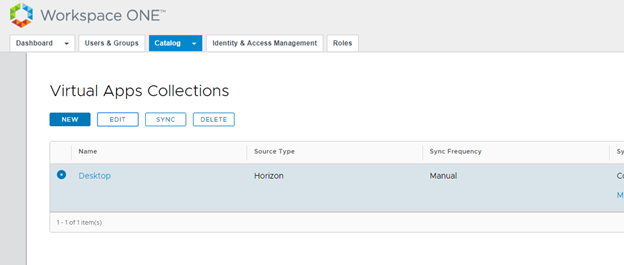
- Login to VMWare Identity Manager admin console and navigate to Catalog> Virtual Apps. Select the Horizon Collection and click Edit
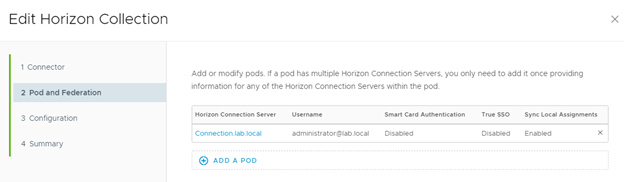
- Click on the existing POD to edit it.
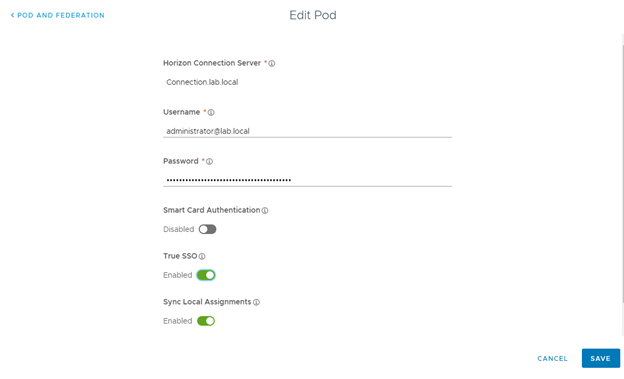
- Now select Enabled for True SSO and Save the POD and Collection.
- Login with user with Radius Auth again and click on Horizon published Desktop.
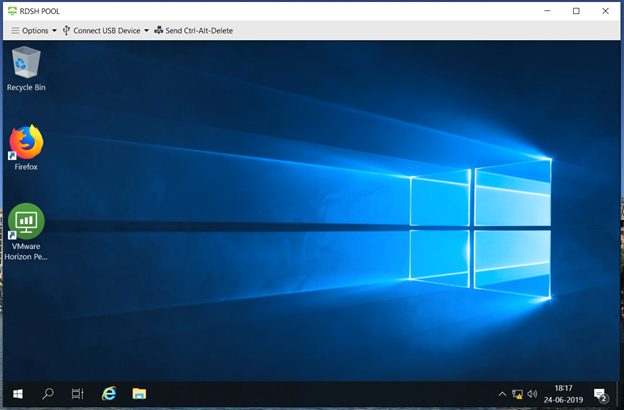
- Desktop will be launched without any prompt for user to enter password as Enrollment server will get SSO certificate from CA on behalf of user which enables seamless login.
Hope, you understood and it will help you in your deployments.
Thanks for reading.