I have been working with multiple customers and there has been a concern to block admin access to local admin user as well as domain users for administration console from Internet. As of now there is no native feature to block this from WS One Access console and requires the implementation of Reverse proxy for such solution. In case, customer doesn’t have Reverse Proxy solution they can leverage on VMware Unified Access gateway as RP for WS One Access. This article talks about the generic configuration where in Proxy patterns doesn’t block admin URL from internet which i have defined in this blog.
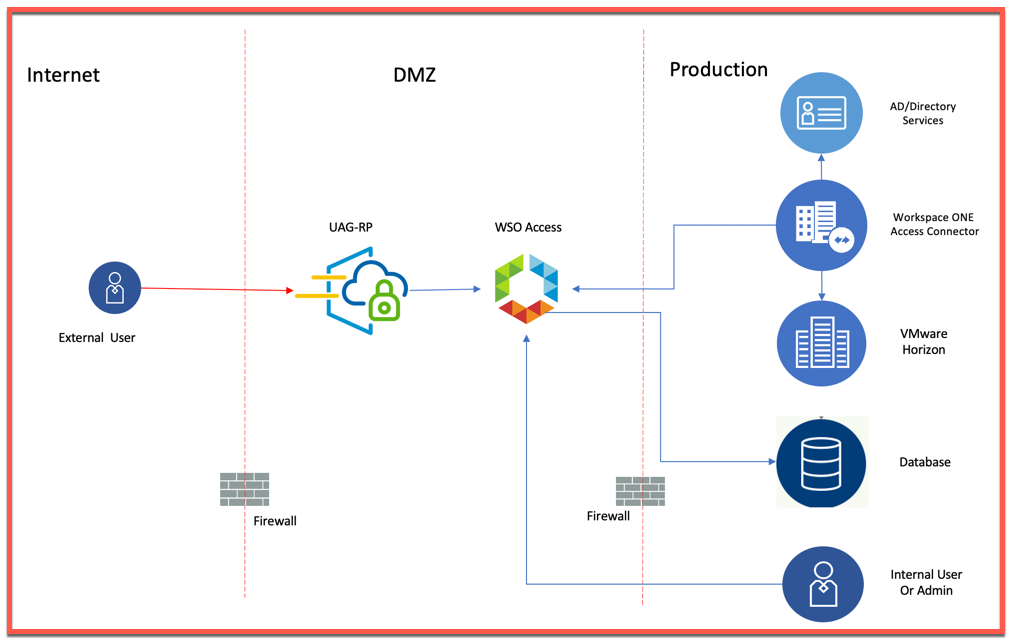
Below is conceptual design where in we are considering Split DNS. i.e. internal users will hit on WSO Access FQDN which will redirect to WSO Access IP (Load Balanced IP in case of HA deployment) and for users, coming in from Internet, they will hit on WSO Access FQDN which will redirect on UAG-RP IP.
Note: This Proxy Pattern is tested for accessing Horizon Virtual Apps from WS One Access Portal and is subject to change depending on more SAAS based apps.
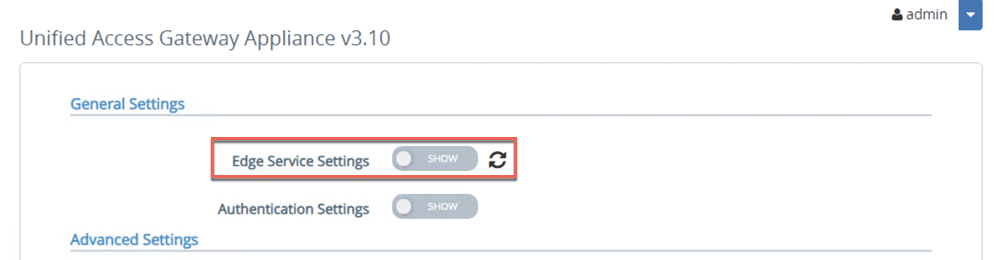
- Login to UAG and click on Show for Edge Service Settings
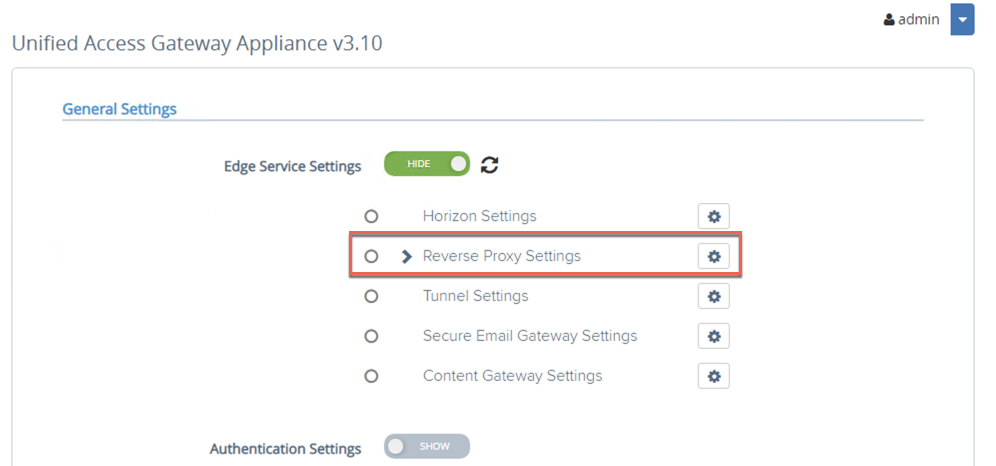
- Click on gear icon corresponding to Reverse Proxy Settings.
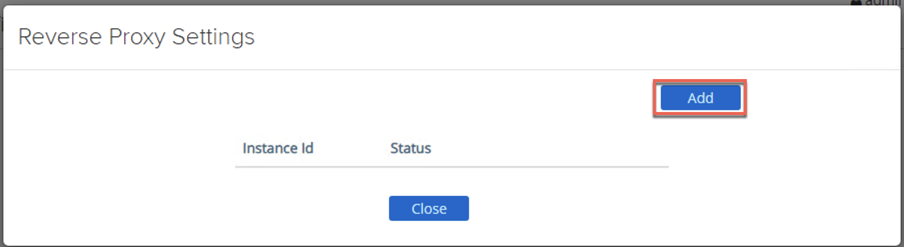
- Click on Add
- Click on Enable Reverse Proxy Settings toggle button to open settings.
- Enter all the data as per this VMware docs article. In order to achieve our objective, we are using different Proxy Pattern which is defined below, then click on Save
Proxy Pattern: (/|/SAAS/auth/logout(.)|/SAAS/auth/login(.)|/catalog-portal(.)|/SAAS/horizon(.)|/SAAS/auth/authenticatedUserDispatcher|/web(.)|/SAAS/apps/|/hc(.)|/SAAS/jersey/manager/api/branding|/SAAS/jersey/manager/api/images/(.*))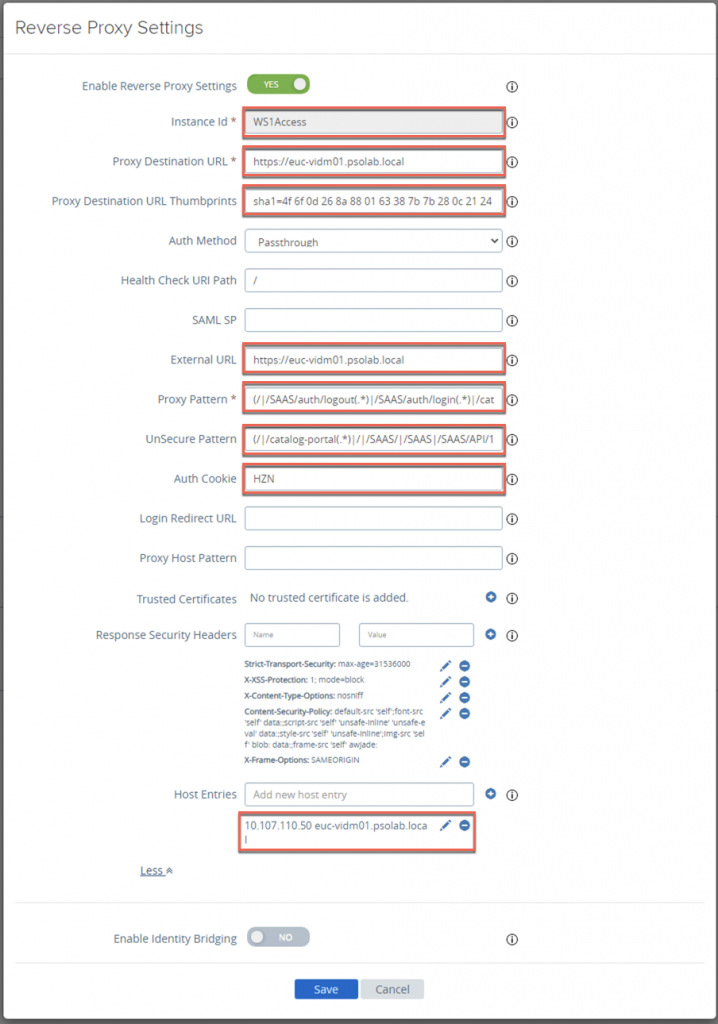
- Refresh your browser to validate that Reverse Proxy is configured and shows green status.
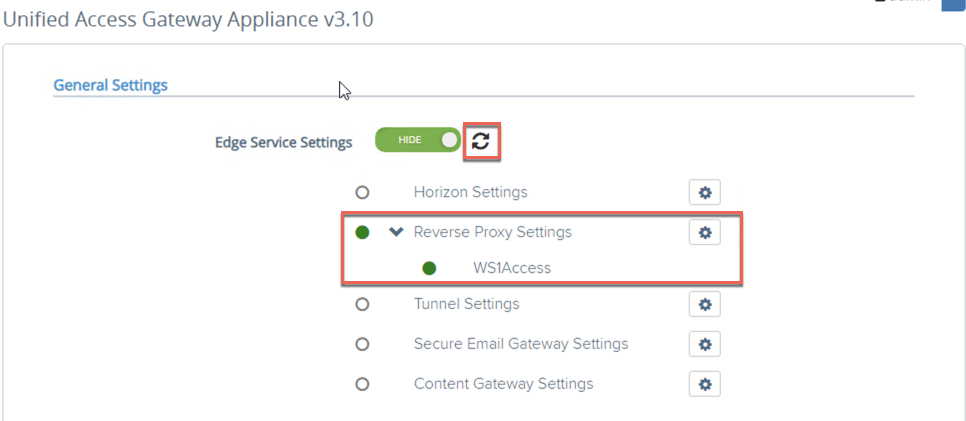
- We need to create DNS record for WS One Access FQDN corresponding to Reverse Proxy UAG IP address in order to route traffic to WS One Access via UAG-RP. Below is video snippet which shows that admin console are blocked from Internet for local admin user as well as for domain admin users when they switch to Administration console
https://<WSOA URL>/SAAS/auth/0 & https://<WSOA URL>/SAAS/login/0
Do let me know your comments or queries.
Note: This is just a prototype and in no case, a reference for production deployment . This also need to be evaluated as per your corporate compliances and security guidelines.

One thought on “WorkSpace One Access with UAG as Reverse Proxy”